Your security team is more than risk insurance. The right operating model, powered by AI, turns security into a partner for product, sales, IT, legal, finance, and engineering. This guide shows how an AI SOC makes that shift practical.
An AI SOC uses machine learning and automation to prioritize alerts, investigate incidents, and execute response playbooks, while generating auditor-ready evidence that maps to SOC 2, ISO 27001, HIPAA, PCI, or any custom framework.
Table of Contents
Why security teams need an AI SOC now
What an AI SOC means
Core building blocks of an AI SOC
High-value AI SOC use cases
Metrics that matter for AI SOC
How to choose an AI SOC platform
Deployment timeline and budget benchmarks
Compliance mapping for AI SOC
Common pitfalls and how to avoid them
Case study: teams reduce MTTD and audit time 40 percent
Next steps and additional resources
Frequently Asked Questions
Why security teams need an AI SOC now
Many companies still treat security as insurance, which leads to underfunding and delays. A better approach views security as experts in technology, software development, risk, and crisis management who improve the whole business.
In earlier models, security liaisons embedded with partner teams helped a lot, but they created bottlenecks and required constant headcount. AI changes the equation. With an AI assistant in the SOC, IT can ask questions, understand requirements, and validate evidence in real time. The assistant has environmental context and will say “I do not know” when data is insufficient, which cuts back-and-forth and removes weeks of delay from evidence review.
Auditors benefit too. Instead of coordinating a “conference” with multiple auditors and senior IT, the AI SOC can answer most requests directly, so people focus on strategic work rather than repetitive tasks.
What an AI SOC means
AI augments analysts at every tier so humans focus on decisions, not data wrangling.
- L1 triage filters duplicates and low-value alerts so analysts spend time on impact.
- L2 investigation enriches cases with identity, cloud, and endpoint context and suggests next steps.
- L3 hunting surfaces weak signals across weeks of telemetry and proposes hypotheses to test.
L1 triage, L2 investigation, L3 hunting with AI assist
- Models score risk using context from identity, cloud, endpoint, email, and network.
- The system summarizes evidence and highlights the decisive artifacts.
- Recommended actions are proposed, with human approvals for sensitive steps.
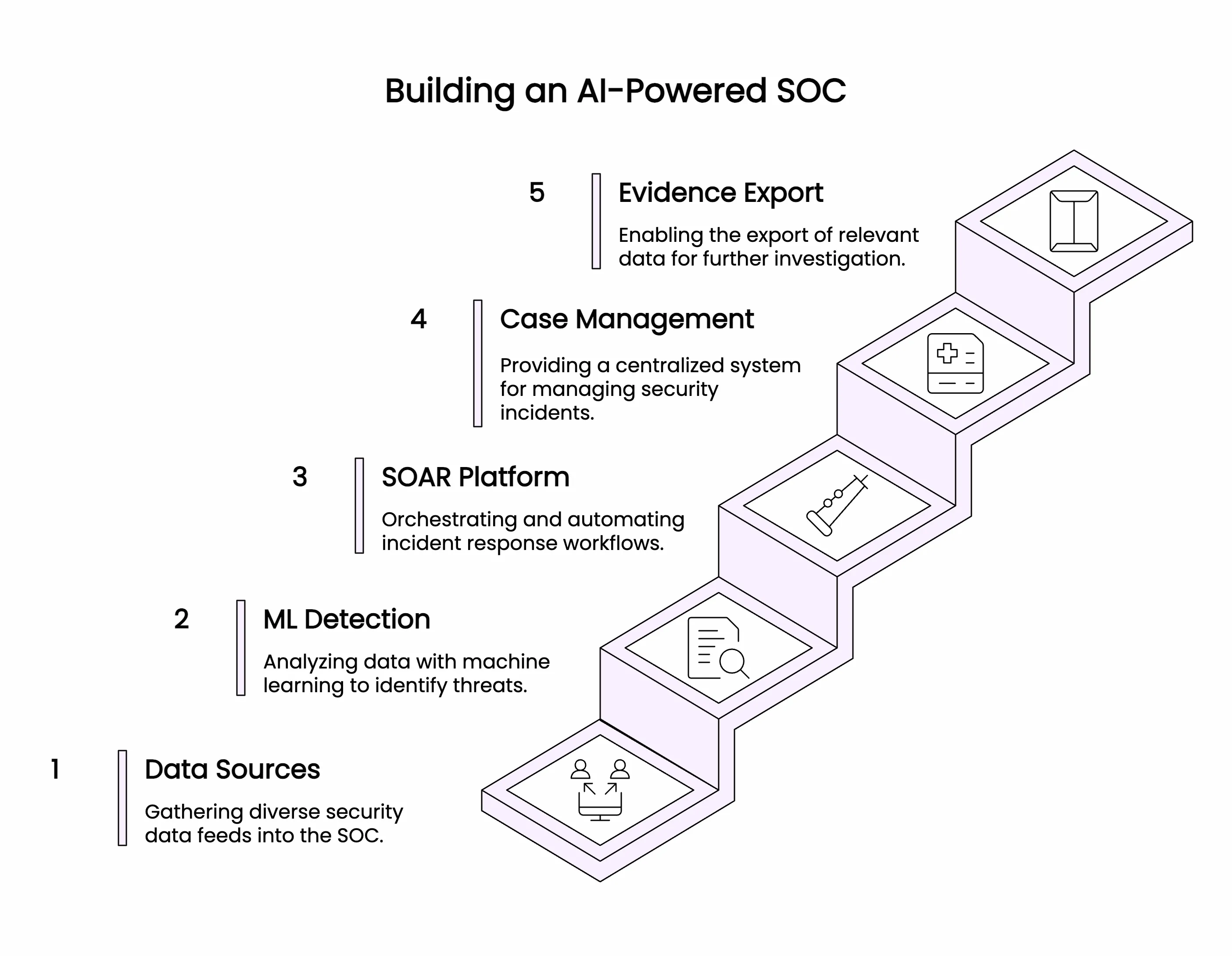
Core building blocks of an AI SOC
- Data lake and connectors, read-only integrations to cloud, identity, endpoint, EDR, email, DNS, network, code, and SaaS.
- ML detections, supervised and behavioral models with explainability.
- SOAR playbooks, containment, credential reset, device quarantine, and ticket creation.
- Case management, ownership, SLAs, evidence vault, and export.
- Safety guardrails, RBAC, approvals, audit logs, and rollback steps.
High-value AI SOC use cases
- Identity threats, impossible travel, MFA fatigue, dormant admin reactivation.
- Cloud misconfiguration, public buckets, risky policies, exposed keys.
- Ransomware, encryption heuristics, mass file changes, lateral movement.
- Insider risk, anomalous downloads, off-hours access, exfiltrations.
- Third-party incidents, vendor breach indicators and blast-radius checks.
Metrics that matter for AI SOC
- Mean Time to Detect, MTTD, and Mean Time to Respond, MTTR.
- Alert precision, true positive rate vs false positive rate.
- Automation rate, percent of steps executed by playbooks.
- Percent of incidents with complete, time-scoped evidence.
- Executive time to decision, how fast leadership gets a clear incident brief.
Publish a weekly scorecard to drive tuning and playbook changes.
How to choose an AI SOC platform
- Accuracy and transparency, see model features, why an alert fired, and confidence.
- Integrations, coverage for your cloud, identity, endpoint, and ticketing tools.
- Playbooks, human-in-the-loop approvals and safe rollback.
- Evidence exports, time-scoped packets mapped to controls.
- Cost, start with a pilot tier and scale by data volume or connectors.
Deployment timeline and budget benchmarks
- Week 1, connect identity, cloud, and endpoint, enable your top 10 detections.
- Weeks 2–3, deploy SOAR playbooks for account reset, device isolate, and ticket open.
- Weeks 4–6, tune models, publish the scorecard, export the first incident packet.
- Budget, begin with pilot licensing, expand with data volume and playbooks.
Compliance mapping for AI SOC
- Map detections and playbooks to SOC 2 CC-series, ISO 27001 Annex A, HIPAA Security Rule, PCI DSS, and any custom framework.
- Export incident packets with logs, hashes, timestamps, owners, and approvals.
- Provide auditors a read-only portal for specific cases.
Common pitfalls and how to avoid them
- Over-automation, require approvals for destructive actions.
- Opaque detections, insist on explainability before enabling.
- No feedback loop, schedule weekly tuning with real false positives.
- Evidence sprawl, store artifacts in an immutable vault with scope tags.
- Unowned alerts, assign owners and SLAs with clear escalation.
Case study: teams reduce MTTD and audit time 40 percent
A mid-size fintech connected identity, cloud, and EDR to its AI SOC.
Result: alert volume down 55 percent, MTTD cut to minutes, and audit prep time reduced by about forty percent due to complete incident packets that auditors could self-serve.
Next steps and additional resources
- Spin up a 30-day pilot, connect three sources, enable three playbooks, and publish a scorecard.
- Reuse incident evidence in audits with these resources:
- SOC 2 mapping: https://trustero.com/products/frameworks/soc2
- ReportScan: https://trustero.com/reportscan
Frequently Asked Questions
- What is an AI SOC
A security operations center that uses ML and automation for detection, investigation, and response with audit-ready evidence. - How does AI reduce alert fatigue
Models cluster duplicates, score risk, and summarize context so analysts act on the highest-impact events. - What data sources feed an AI SOC
Identity providers, cloud platforms, EDR, email, DNS, network, code repositories, and SaaS, all read-only. - Can an AI SOC help with SOC 2 and ISO 27001
Yes. Detections and playbooks map directly to controls and provide time-scoped artifacts for auditors. - How do I measure AI SOC success
Track MTTD, MTTR, precision, automation rate, and percent of cases with complete evidence. - What is the typical deployment timeline
Pilot in weeks, scale in a quarter, with tuning and scorecards each sprint.
Ready to launch your AI SOC? Book a 15-minute Trustero walkthrough and get an actionable deployment plan.

