SOC 2 compliance is a critical foundation for consistent, transparent processes that enable verifiable trust among your most critical stakeholders – your customers, partners, and prospects. Preparing well for a SOC 2 compliance audit can make the entire process faster, easier, less expensive, and less disruptive to your business operations. It can also ensure that your company passes the audit, receives a report that your stakeholders will trust and accept, and lays a firm foundation for sustained compliance.
Here are ten questions you and your colleagues should answer to ensure your progress toward a successful SOC 2 audit.
Why Are Your Stakeholders Asking for SOC 2 Compliance?
Your customers and business partners want to know that your company can protect their data and yours. SOC 2 compliance provides independently verified validation that your company has put into place people, policies, procedures, processes, and tools that provide adequate protection for your information systems and the data that passes through them.
Do You Understand What's Required?
SOC 2 is based on five Trust Service Criteria – Security, Availability, Processing Integrity, Confidentiality, and Privacy. Those criteria embrace some 64 more granular requirements, each of which can require multiple controls, which can be policies, procedures, or processes, to be addressed effectively. Your business may need as many as 100 controls to address the Security criterion requirements successfully.
Your team must carefully evaluate your specific goals for SOC 2 compliance then map these to the appropriate Trust Service Criteria and related requirements. For many companies, the Security criterion is the highest priority, as it directly affects the ability to enable adequate levels of Confidentiality and Privacy.
Do You Have the Right People Involved?
Your SOC 2 preparation team should include senior members of your engineering, HR, IT, legal, and physical security teams or departments. This will ensure all the critical business processes affected by your compliance efforts will be represented throughout your pursuit of compliance.
Does Your Organization Follow the Policies, Procedures, and Processes as Published?
The policies, processes, and procedures used to achieve and sustain SOC 2 compliance are known collectively within the SOC framework as “controls.” Those controls that govern your critical business operations will all likely be affected by or influence your company’s pursuit of SOC 2 compliance. For example, if those policies, processes, and procedures are inconsistently implemented, enforced, or documented, your efforts to achieve compliance could be impeded or made impossible. Conversely, the pursuit of SOC 2 compliance could be the impetus for your company to improve the quality and consistency of its most critical policies, processes, and procedures.
Do You Have the Right Technologies in Place?
Achieving and sustaining SOC 2 compliance requires consistent, comprehensive monitoring of almost every element of your organization’s information infrastructure. The more effective, integrated abilities you have to monitor and report on the health and security of your IT environment, the less challenging it will be to meet your SOC 2 requirements. A platform that can help your company achieve and sustain compliance can be a powerful asset.
As with your internal controls, the pursuit of SOC 2 compliance may provide an incentive for your organization to implement or improve your incumbent relevant monitoring, reporting, and compliance management technologies.
Have You Consulted with Your Business Partners?
Your business partners or supply chain connections, especially if they are larger enterprises, may already be SOC 2 compliant. They may also have specific compliance requirements or expectations of your organization. Consulting with their compliance leaders can provide useful guidance for your own organization’s SOC 2 compliance efforts. In some cases, one or more of your company’s supply chain partners may be able to provide a Security Questionnaire for you to complete. The good news here? Once you attain SOC 2 compliance, you can frequently submit your compliance report in lieu of completing more Security Questionnaires.
Are You Ready to Perform a Self-Assessment?
You cannot and should not wait until your SOC 2 auditors show up at your door to assess your organization’s readiness. A detailed self-assessment can ease and speed your journey to full SOC 2 compliance. This is especially true if you already have people, policies, procedures, and processes focused on governance, risk, and compliance (GRC) or similar areas. Such resources may help you complete your self-assessment more quickly.
Your business will also need to designate or hire someone to lead your self-assessment. But the effort and expense will provide valuable and useful information about your organization’s compliance readiness.
Can You Close the Gaps You Discover Before Your Audit?
Your self-assessment will almost definitely discover multiple gaps between the state of your organization and its requirements for SOC 2 compliance. As a result, your organization may need to modify incumbent policies, procedures, and processes or craft missing ones. You may also discover opportunities or needs to modify incumbent or create missing workflows, within or beyond IT. This is one of the areas in which executive leadership support may be most needed and valuable, as closing discovered gaps will likely require significant investment.
Are You Committed to Sustained Compliance?
SOC 2 compliance is not a “one and done” exercise. To sustain compliance, your organization will need to be audited annually. In addition, SOC 2 is unlikely to be the only compliance challenge your organization faces or will face. The lessons you learn from your first audit must be used to inform both future SOC 2 audits and any other compliance efforts at your organization.
Have You Engaged an Auditor?
You will need to find and hire an auditor to prepare for and execute your first SOC 2 audit, and for every audit thereafter. Your preparation efforts should therefore include exploration of your available alternatives where your ultimate choice of an auditor is concerned.
Your current accountant may be a CPA, but may not be certified to perform a SOC 2 audit. However, your CPA may be able to supply references to appropriate candidate auditors. Industry colleagues who have achieved SOC 2 compliance may also be sources of useful referrals. However you identify your candidates, you should never choose based on price alone. Instead, you should look for candidates with strong customer references, and preferably experience with businesses like yours.
Next Steps
Once you have successfully answered these 10 questions, you’re ready to dig more deeply into your organization’s specific compliance requirements, based on detailed exploration of SOC 2, the Trust Service Criteria, and their underlying requirements. You should also begin looking at candidate compliance automation software solutions and their vendors.
As with your auditor search, avoid being swayed by pitches that focus on low cost or rapid resolutions. Instead, look for offerings that promise results that match your needs and your chosen auditor’s workflows most closely, and that minimize the need for extensive additional investment in hardware, software, or services.
How Trustero Can Help
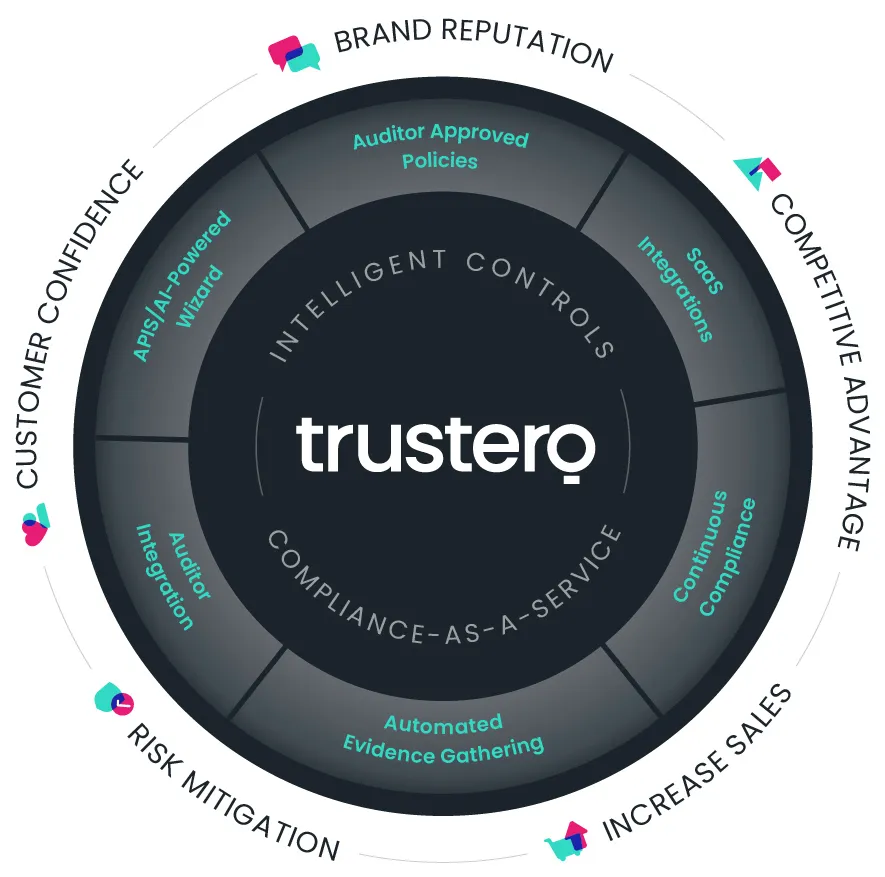
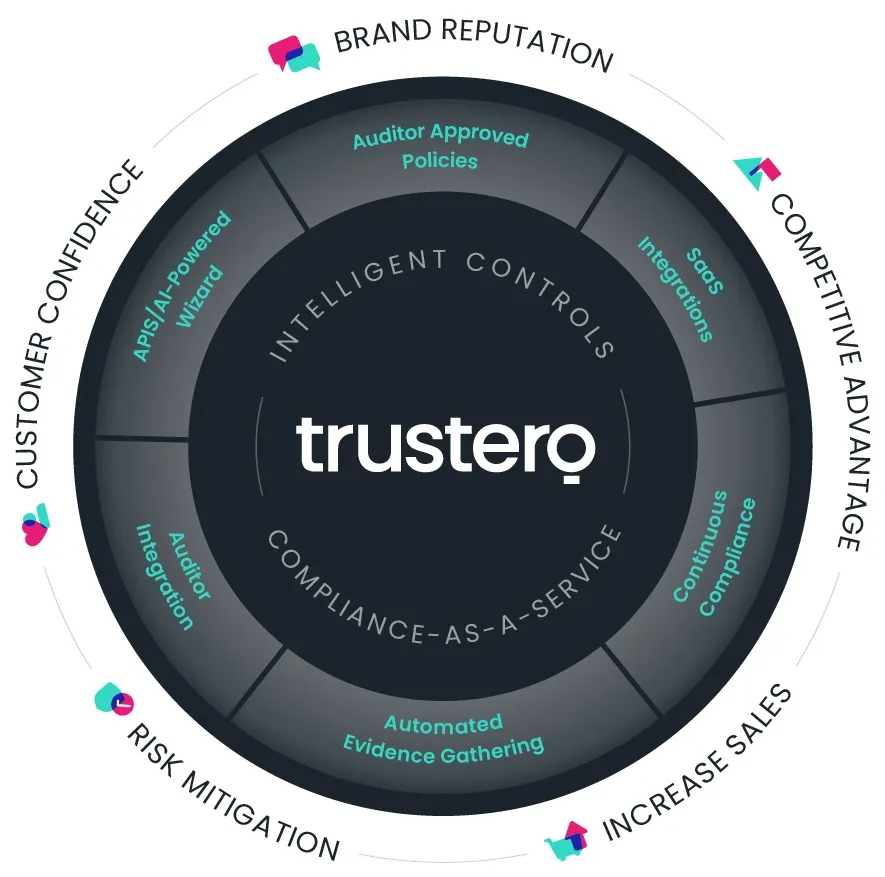
Trustero combines cloud computing, patent-pending artificial intelligence (AI), and other modern technologies to deliver Compliance as a Service. This approach helps you become compliant and keep your critical business policies and practices intact and in place, to save your company time and money, today and for every future SOC 2 compliance audit. Trustero’s solution works with you and your trusted auditor to achieve and sustain SOC 2 compliance, effectively, efficiently, and economically. Our engineers have solved complex security and scale problems at companies such as Facebook and SignalFx.