HIPAA protects the privacy and security of patient information. When organizations fall short, the HHS Office for Civil Rights, OCR, investigates and may require corrective actions, monitoring, and fines. This guide explains what triggers penalties, how much they can cost, and how to avoid them with strong controls and proof.
HIPAA penalties are civil or criminal fines issued after violations of the Privacy, Security, or Breach Notification Rules, with civil money penalties assigned in four tiers by culpability and adjusted annually, plus potential criminal charges for intentional misuse of protected health information.
Table of Contents
1. What counts as HIPAA noncompliance2. Who enforces HIPAA and how investigations work
3. Civil Money Penalty tiers and fine ranges
4. Criminal penalties, fines, and jail time
5. Common violations and case examples
6. Breach reporting timelines and penalty triggers
7. State AG actions and class actions
8. How to avoid penalties: policies, training, and proof of controls
9. Evidence you need if OCR asks
10. Next steps and additional resources
11. Frequently Asked Questions
What counts as HIPAA noncompliance
Failing to protect PHI with reasonable and appropriate safeguards.
Not completing or maintaining an enterprise risk analysis and risk management plan.
Not limiting access to the minimum necessary or lacking unique logins and MFA.
Missing or late breach notifications.
No Business Associate Agreements, BAAs, with vendors that touch PHI.
Not keeping required policies, training records, audit logs, and documentation.
Who enforces HIPAA and how investigations work
OCR investigates complaints, breach reports, and referrals. Outcomes include technical assistance, corrective action plans with monitoring, resolution agreements, or civil money penalties. The Department of Justice handles criminal cases. State Attorneys General can bring separate actions, and class actions may follow large breaches.
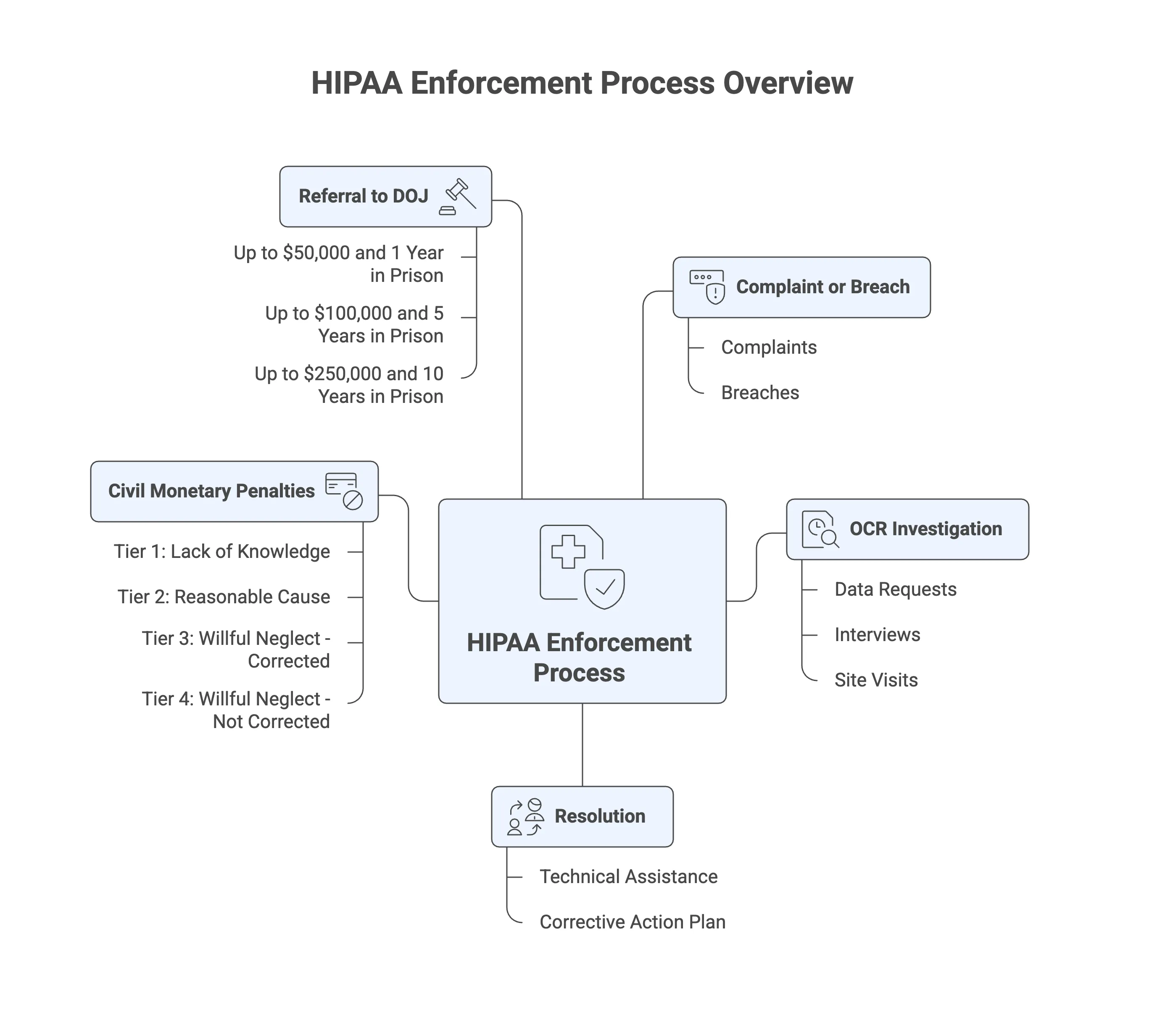
Civil Money Penalty tiers and fine ranges
Penalties are assessed per violation, scale by culpability, and have annual caps that HHS updates for inflation. Typical ranges used by organizations for planning are:
Tier 1, lack of knowledge: about $100 to $50,000 per violation.
Tier 2, reasonable cause: about $1,000 to $50,000 per violation.
Tier 3, willful neglect corrected within the required time: about $10,000 to $50,000 per violation.
Tier 4, willful neglect not corrected: $50,000 per violation and the highest potential annual caps.
Document the version and publication date of the HHS ranges you use in training and policies.
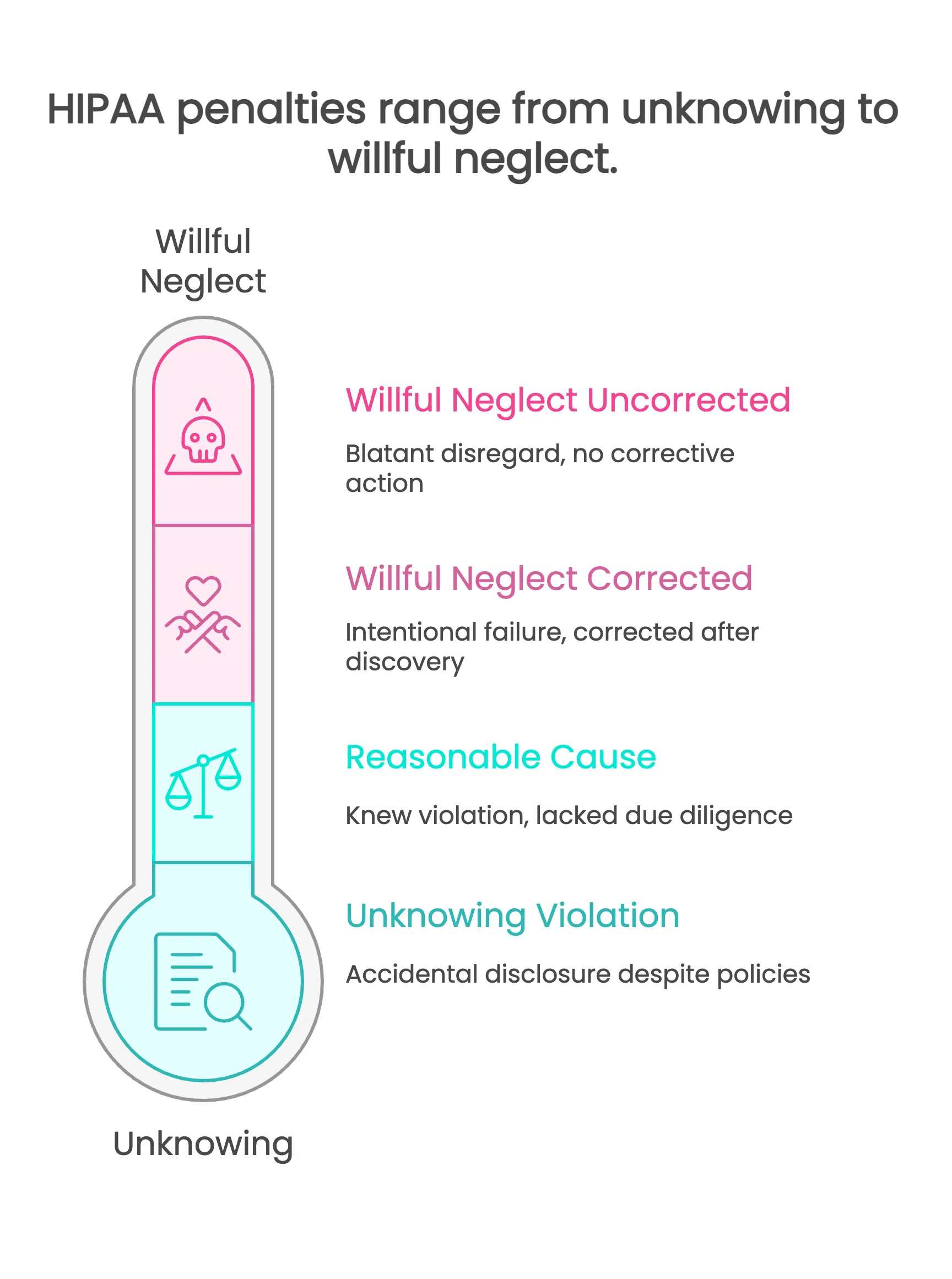
Criminal penalties, fines, and jail time
1. Intentional misuse or disclosure of PHI can trigger DOJ action.
2. Improper access or disclosure: fines and up to 1 year imprisonment.
3. False pretenses: larger fines and up to 5 years imprisonment.
4. For personal gain, commercial advantage, or malicious harm: the largest fines and up to 10 years imprisonment.
5. Maintain sanctions policies and workforce awareness so violations are handled consistently.
Common violations and case examples
1. No or incomplete risk analysis and risk treatment plan.
2. Lost unencrypted laptops or cloud buckets with PHI.
3. Excessive access, shared accounts, or missing terminations.
4. Weak logging, monitoring, or alerting.
5. Missing BAAs with vendors who process PHI.
6. Late or incomplete breach notifications.
7. Undocumented training and sanctions.
Breach reporting timelines and penalty triggers
Notify affected individuals without unreasonable delay and no later than 60 days after discovery.
Notify HHS on the same timeline for incidents affecting 500 or more individuals and notify local media.
For fewer than 500, report to HHS within 60 days after the end of the calendar year.
Keep written determinations of whether PHI was compromised, scope of data, harm evaluation, and mitigation steps.
State AG actions and class actions
States can enforce privacy and security rules independently and may have shorter notification timelines. Large breaches can trigger class actions. Track multi-jurisdiction requirements and coordinate legal counsel and communications.
How to avoid penalties: policies, training, and proof of controls
Run an enterprise risk analysis and refresh it regularly.
Maintain BAAs for every vendor that can access PHI.
Enforce least privilege, unique logins, MFA, encryption at rest and in transit.
Enable audit logging, review logs, and retain records as required.
Train the workforce on policies and sanctions.
Test incident response and breach notification playbooks.
Automate daily checks and keep time-scoped evidence in a tamper-evident vault.
Evidence you need if OCR asks
1. Enterprise risk analysis and risk management plan.
2. Security and privacy policies and procedures.
3. Access reviews, termination records, and privilege-change approvals.
4. Audit logs for access, changes, backups, and alerts.
5. Training rosters, materials, and attestations.
6. Business associate inventory and signed BAAs.
7. Incident records, breach determinations, and notification proofs.
8. A single evidence map that ties each safeguard to the HIPAA Security Rule.
Next steps and additional resources
1. Publish an evidence calendar with owners and due dates.
2. Stand up read-only integrations for cloud, identity, endpoint, email, and backups.
3. Run quarterly self-audits and remediate gaps with deadlines.
4. Link to policy packs, a BAA checklist, and incident response playbooks.
5. Map HIPAA safeguards to SOC 2 and ISO 27001 so one control test satisfies many programs.
Frequently Asked Questions
1. Civil penalty tiers and amounts
Four tiers from lack of knowledge to willful neglect not corrected, with per-violation fines that HHS adjusts annually and caps per year for identical violations.
2. Civil vs criminal penalties
Civil penalties are assessed by OCR. Criminal charges are handled by DOJ for intentional misuse, false pretenses, or personal gain.
3. Breach reporting deadlines
Notify individuals and HHS without unreasonable delay and no later than 60 days. Smaller breaches are reported to HHS annually.
4. BA liability
Business associates and their subcontractors are directly liable. Covered entities must have BAAs and ongoing oversight.
5. How to reduce penalty exposure
Do a current risk analysis, enforce encryption and MFA, review access, train the workforce, monitor logs, and keep time-scoped proof of control operation.
6. Evidence needed for OCR
Risk analysis, policies, training logs, access reviews, audit logs, BA inventory and BAAs, incident timelines, and notification proofs.
How Trustero helps
Continuous control assurance runs daily tests for encryption, MFA, access reviews, backups, and logging. A tamper-evident evidence vault stores time-scoped artifacts mapped to HIPAA safeguards, SOC 2, ISO 27001, PCI DSS, and any custom framework. Auditors and counsel can access a read-only portal or export complete packets during investigations.
Call to action
Worried about HIPAA fines? Book a 15 minute Trustero demo and see how automated control testing and real time evidence reduce penalty risk.

